Archive
Deque Implementation Design
For Assignment 1 of COMP2911 we got the task of implementing a deque, using arrays and linked lists (in Java). Here is the design I used for the implementation.
ArrayDeque
This was quite a challenge.
One approach was to have an array of size capacity, and also store some left and right index pointers to know where the deque ranges in the array.
My first idea (actually inspired by my tutor) was basically, to add to the right of the deque you start at the left and push right, to add to the left of the deque you start at the right and push left. When the two ends collide, you make a new array larger keeping the left and right parts of the deque at the leftmost and rightmost parts of the array.
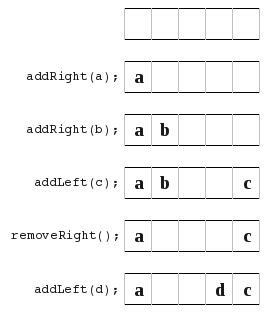 This turned out to have some problems. All worked well, except for a couple of things. Such as show here,
This turned out to have some problems. All worked well, except for a couple of things. Such as show here,
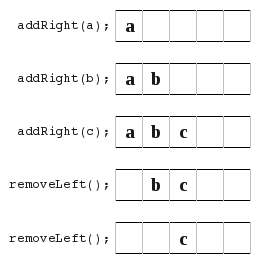 , because now you are left in the middle and your not just pushing straight from one side to another.
, because now you are left in the middle and your not just pushing straight from one side to another.
This next situation below was also troublesome because you have to be careful where you store your left/right index pointers. You need to carefully think of what if they overlap? And if they are equal or overlap, is your arrayDeque full or empty?
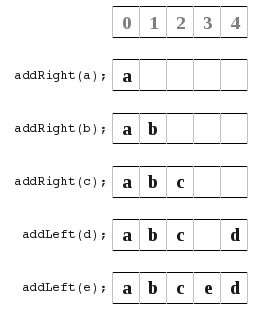 So what I did is look at the different ways to store the left/right index pointers. In all these diagrams orange means the location of the left index pointer, and the violet is the location of the right index pointer.
So what I did is look at the different ways to store the left/right index pointers. In all these diagrams orange means the location of the left index pointer, and the violet is the location of the right index pointer.
a) In this diagram I point to the next available space.
 b) In this diagram I point to the location of the most recently added item. At the very beginning I loop them over.
b) In this diagram I point to the location of the most recently added item. At the very beginning I loop them over.
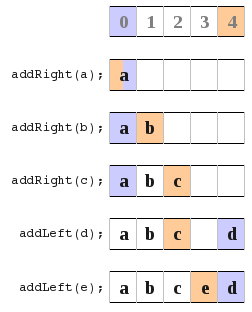 All this just lead to much confusion for me and many bugs and problems. So I had a look at an entirely new approach. It turned out much better, and I learnt that if things aren’t working out and you just keep getting lots of bugs then sometimes trying another approach can really help out. I also learnt that its really hard to know the best way to do something right from the start you really have to try something and if its not working to well than just try something else and see how it goes. So here is what I finally did.
All this just lead to much confusion for me and many bugs and problems. So I had a look at an entirely new approach. It turned out much better, and I learnt that if things aren’t working out and you just keep getting lots of bugs then sometimes trying another approach can really help out. I also learnt that its really hard to know the best way to do something right from the start you really have to try something and if its not working to well than just try something else and see how it goes. So here is what I finally did.
 Initially I just ignored the fact that I had a limited size array, and that things are actually mod array size. I just had two index pointers (shown in orange and blue) which pointed to the next free space at the left and right ends of the deque. I kept these as ints and they I don’t think of them as wrapping round. If you forget about the array based implementation and go back to the original problem of a deque you see that really all you need is a big long line with a left end and right end pointer. Now all you have to do is remember that whenever you are dealing with implementation level things such as accessing the array, to use index mod capacity, rather than the raw index value (which may be out of the array range). That and you need to have a check to know when to resize your array.
Initially I just ignored the fact that I had a limited size array, and that things are actually mod array size. I just had two index pointers (shown in orange and blue) which pointed to the next free space at the left and right ends of the deque. I kept these as ints and they I don’t think of them as wrapping round. If you forget about the array based implementation and go back to the original problem of a deque you see that really all you need is a big long line with a left end and right end pointer. Now all you have to do is remember that whenever you are dealing with implementation level things such as accessing the array, to use index mod capacity, rather than the raw index value (which may be out of the array range). That and you need to have a check to know when to resize your array.
Under this scheme the number of items in your deque is rightIndex – leftIndex – 1, therefore your array is full if and only if (rightIndex – leftIndex – 1) >= capacity. (Where capacity is the size of the array). If this is true then you need to resize your array.
The method I choose was to simply shift the deque along (either direction) so that the leftIndex is at -1.
LinkedDeque
This was much simpler. Basically I made a link object that stored an item and a left and a right pointer (to other link objects). I would store the leftmost and rightmost link items for the deque and that is all. I guess I could have stored size as part of the deque object and updated it whenever new link items were added or removed to the deque, but as we were given no requirements to do it one way or another I made it so that the size method would go though the whole deque and do a summation every time it was called.
The only thing I really had to watch was to ensure that I kept the left and right pointers for each link item up to date with changes, and this was my primary source of bugs.
Very Useful Ubuntu/Unix Commands
Just some Ubuntu/Unix commands that I seem to find very useful but can be hard to remember at times.
PDF Concatenation
pdftk in1.pdf in2.pdf cat output out1.pdf
Its annoying that nautilus doesn’t integrate this by default, so I could select some PDF’s then right click and choose merge. Luckily I can do this with the fairly simple Nautilus Actions Configuration app. But this takes time and the average user doesn’t have the time to research these things on how to do it themselves. Of course this could be extended further to match what you can do from the command line, such as choose some method of ordering the files, or choose to do weird things such as rotate every second page. Sure you want to keep things simple, so as a start it would be great to see something basic. There are probably even nautilus scripts in the repositories out there that do this exact thing, but you spend half your time finding them and installing them. I think this should be enabled by default, or put in some options page somewhere.
Truncate an mp3 file
mpgsplit input.mp3 [00:00:20-00:00:58] -o output.mp3
It appears that this doesn’t re-encode so it seems to run very fast.
Mount an ISO
sudo mount -o loop ~/disk.iso /media/cdrom0
Strip audio from a video file
ffmpeg -ab 320k -i in.mov outaudio.mp3
Unfortunately when I left out the bit rate, it defaulted to 14K or something much lower than what the source file was using.
Search all files in the current directory for some string
find . -exec grep "searchthisstring" '{}' \; -print
find . -exec grep -q "searchthisstring" '{}' \; -print
Trim and nup pdfs
pdfnup --nup 2x2 --pages 26-140 --trim "1cm 1cm 1cm 1cm" infile.pdf
Wake from Suspend
sudo rtcwake -u -s 12600 -m on
… then you need to manually put the computer in suspend and 12600 seconds later the computer will resume.
Susped
pm-suspend
Shutdown
sudo shutdown -h now
sudo shutdown -r now
… the -h means halt (shutdown), -r means reboot.
Tar and Gz all the files in a directory
tar -cvfz file.tar.gz *
Get file info from an HTTP server without downloading
wget -S --spider http://www.site.com/file
SBS Latest Online Video RSS Feed
[An updated (but more complex) script can be found in this post]
I needed an excuse to practice some Perl. So this was my first try.
The Perl script below will convert http://www.sbs.com.au/shows/ajax/getplaylist/playlistId/94/ to an RSS feed. That 94 playlist is a list recent episodes from the TV broadcaster SBS available online. This may not work if the source file’s structure changes.
#!/usr/bin/perl
# This script will download the ajax xml file containing the latest full episode videos added to the SBS.com.au site.
#Adapted from the code at http://www.perl.com/pub/a/2001/11/15/creatingrss.html by Chris Ball.
# I declar this code to be in the public domain.
# THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
# IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
# FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
# AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
# LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
# OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
# THE SOFTWARE.
use strict;
use warnings;
use LWP::Simple;
use HTML::TokeParser;
use XML::RSS;
use Date::Format;
# Constants
my $playlisturl = "http://www.sbs.com.au/shows/ajax/getplaylist/playlistId/94/"; # Latest Full Ep
#my $playlisturl = "http://www.sbs.com.au/shows/ajax/getplaylist/playlistId/95/"; # Latest Sneek Peek
# LWP::Simple Download the xml file using get();.
my $content = get( $playlisturl ) or die $!;
# Create a TokeParser object, using our downloaded HTML.
my $stream = HTML::TokeParser->new( \$content ) or die $!;
# Create the RSS object.
my $rss = XML::RSS->new( version => '2.0' );
# Prep the RSS.
$rss->channel(
title => "SBS Latest Full Episodes",
link => $playlisturl,
language => 'en',
lastBulidDate => time2str("%a, %d %b %Y %T GMT", time),
description => "Gives the most recent full episodes avaliable from SBS.com.au"
);
$rss->image(
title => "sbs.com.au Latest Full Episodes",
url => "http://www.sbs.com.au/web/images/sbslogo_footer.jpg",
link => $playlisturl
);
# Declare variables.
my ($tag);
# vars from sbs xml
my ($eptitle, $epthumb, $eptime, $baseurl, $img, $url128, $url300, $url1000, $code1char, $code2char, $code1);
#get_tag skips forward in the HTML from our current position to the tag specified, and
#get_trimmed_text will grab plaintext from the current position to the end position specified.
# Find an <a> tag.
while ( $tag = $stream->get_tag("a") ) {
# Inside this loop, $tag is at a <a> tag.
# But do we have a "title" token, too?
if ($tag->[1]{title}) {
# We do!
$eptitle = $tag->[1]{title};
#print $eptitle."\n";
# The next step is an <img></img> set.
$tag = $stream->get_tag('img');
$epthumb = $tag->[1]{src};
#get the flv urls from the img url
#eg. http://videocdn.sbs.com.au/u/thumbnails/SRS_FE_Global_Village_Ep_19_44_48467.jpg
#print $epthumb."\n";
$baseurl = substr($epthumb, 40, length($epthumb)-40-4);
$url128 = "http://videocdn.sbs.com.au/u/video/".$baseurl."_128K.flv";
$url300 = "http://videocdn.sbs.com.au/u/video/".$baseurl."_300K.flv";
$url1000 = "http://videocdn.sbs.com.au/u/video/".$baseurl."_1000K.flv";
#SRS|DOC|MOV
$code1char = substr($baseurl,0,3);
#SP|FE
$code2char = substr($baseurl,4,2);
my %epcode_hash = (
'DOC' => 'Documentary',
'MOV' => 'Movie',
'SRS' => 'Series',
);
$code1 = $epcode_hash{$code1char};
$stream->get_tag('a');
$tag = $stream->get_tag('p');
# Now we can grab $eptime, by using get_trimmed_text
# up to the close of the <p> tag.
$eptime = $stream->get_trimmed_text('/p');
# We need to escape ampersands, as they start entity references in XML.
$eptime =~ s/&/&/g;
# Add the item to the RSS feed.
$rss->add_item(
title => $eptitle,
permaLink => $url1000,
enclosure => { url=>$url1000, type=>"video/x-flv"},
description => "<![CDATA[<img src=\"$epthumb\" width=\"100\" height=\"56\" /><br>
$eptitle<br>
$eptime<br>
Links: <a href=\"$url128\">128k</a>, <a href=\"$url300\">300k</a>, <a href=\"$url1000\">1000k</a><br>
Type: $code1<br>]]>");
}
}
print "Content-Type: application/xml; charset=ISO-8859-1"; # To help your browser display the feed better in your browser.
#$rss->save("sbslatestfullep.rss"); #this will save the RSS XML feed to a file when you run the script.
print $rss->as_string; #this will send the RSS XML feed to stdout when you run the script.
SENG4921 – Oral Exam Prep
Here are the notes I made for and took into the SENG4921 oral exam.
As an after thought, you can see I wasn’t prepared for all the options but this is the best I could do in the time. Some of my arguments here may not be very valid, but this is my preparation as it stands, not a blog post into the questions (that’s my excuse for being sloppy).
Question 1: free choice
- “Each student should prepare a topic of their own free choice concerned with some aspect of software, hardware, IT professional issues or ethics. This could be —but does not have to be— based on, or derived from, the discussions, seminars, debates, student run seminars and lectures given this semester. The question should be broad enough to not overlap with the other two questions. At the examination the student will be asked to present his/her topic and discussion.
If the free choice question deals directly with one of the Seminar or Lecture questions, then this will generally eliminate that question if one of the randomly chosen 3 for question 2 or 3. Note carefully that the elimination occurs after the random choice, not before.”
After a little thought I think I will focus on DRM in this question. I think this is a good choice because,
- Its not covered in the other seminar and lecture questions,
- I know enough about the topic to be able to talk about it,
- There are actually some valid ethical questions that can be raised and debated here,
- …
So the deal is I only have 5 minutes to talk about the professional issues and ethics surrounding DRM. I need to identify the issues involved, analyse the professional and/or ethical consequences and present the outcome. I will need to be careful that I address the right things as I only have 5 minutes.
The examiners will be looking for:
- clear identification of the issues;
- analysis of the professional and/or ethical consequences;
- careful presentation of the outcomes.
There are no correct answers, but a good answer will give a clear indication of consequences and issues.
Identification of Issues
DRM is digital rights management. DRM technologies attempt to control use of digital media by preventing access, copying or conversion to other formats by end users.
- DRM is used to bypass existing copyright laws and create your own. Content protected by DRM uses software or hardware measures to prevent unauthorised use of such content. An example is protected music purchased from the iTunes music store. The music is usually encoded using AAC, however on top of this it is encrypted. In simple terms you can only play this music on Apple approved devices. So you cannot play that music on a sony MP3 player, you cannot convert the music to MP3, you cannot play the music on another player on Linux, and lastly if Apple goes bust and decides not to free your music you will never be able to play the music you bought.
- How different is this to selling music using patented encoding techniques. No one else is allowed to make a player except you.
- I mentioned this bypasses existing copyright laws. An example of this is say you want to use a segment of the content you bought which is protected by DRM but the use of the segment is permitted under copyright laws. Regardless of the law you can’t use the material either because you can’t crack the DRM or even if you can, the process of doing so is illegal.
- Also most DRM systems are not set to expire when they are supposed to fall into the public domain. Thus the work may be public domain but no one can access it as its encrypted with some DRM mechanism and no keys no longer available. This undermines the concept of the public domain.
Lastly DRM systems do not work, as most have been cracked. Once the DRM has been cracked by one person (who may be an expert) then can distribute this clean version to all over say BitTorrent. DVD’s CSS was cracked,
From personal experience a while ago I downloaded an e-book (actually a standards document) from the UNSW library/publisher of the standard. It was a PDF document and they told me that it would expire after a week or so. It turns out that it used some JavaScript hide the text when the system date was at whatever was a week after the PDF was downloaded (so the web server was creating the PDF on the fly putting the expiry date and the download details into the PDF). This could be easily bypassed by disabling JavaScript, using a free PDF reader that does not support JavaSript, and so on. Furthermore you could easily use some software to extract the content of the PDF and resave it without the DRM. (Will I go to jail if I ever vist the US because of the DMCA?? Or even from Australian laws?)
Professional and/or ethical consequences
Ken noted in his introduction article that “In this course, we will be particularly concerned with developing your capacity to reason about the possible outcomes.” Hence I will try to focus on the affects/consequences of DRM. Taking a consequential approach to ethical thinking requires one to consider the possible consequences. So some consequences of DRM that should be addressed when taking a ethical approach to DRM are,
- Legitimate users soon find out that they can only use the products they thought they bought in situations that are approved. eg. you find out that your iTunes music won’t play on Linux.
- Consumers become locked in to one vendor. eg. they may have purchased $100 worth of music, but they find they must buy an Apple MP3 player to use it and cannot shop around. Companies can use this advantage to raise the prices of their products to above market value.
- DRM systems that require a ‘call back’ over the internet to some key server won’t work if the company goes bust. Hence if the company goes, so does all your music.
- Many consumers will be driven to consume pirated material as its generally DRM free so less hassles.
- The public may turn against corporations as a whole, due to those that have abused their honesty and good will. People may loose trust in companies and no longer purchase any material and just obtain pirated materials instead.
- Consumers/public may feel coned and abused.
These are all possible outcomes, yet they may not all be an ethical concern. This depends on your individual ethical principles. For me if DRM leads people to move to pirated material rather than paying the owner, then this under my ethical principles this is not a concern. This is strictly a business move and the consumer will not be harmed by doing this. If the company doesn’t want people to pirate the matrial instead of buying it then they can simply remove their DRM and sell it DRM free.
But from a utilitarian perspective, DRM does little to stop the original creator receiving remuneration (if anything it may result in less remuneration), instead it causes great unhappiness. In this respect it is unethical.
As Cohen outlined professions come with these extra “professional” responsibilities. Including “public interest is paramount”, public trust, but also client’s interests. Most (if not all) DRM systems are not in the public’s interest. They are riddled with problems and do very little to stop piracy. They turn honest customers into outlaws. The key thing that consumers need to be aware of is they are not purchasing products from the iTunes store rather they are purchasing a licence to use the music in a restricted set of conditions.
Question 2: Seminar Questions
1. “Engineering”
I think Wikipedia’s summary of Engineering describes what is generally understood by the term ‘Engineering’.
Engineering is the application of scientific and technical knowledge to solve human problems. Engineers use imagination, judgement, reasoning and experience to apply science, technology, mathematics, and practical experience. The result is the design, production, and operation of useful objects or processes.
Of course as a profession it comes with all the things that make it a professions such as responsibility to the public, client’s interest, public trust, an so on.
Software and Computer Engineering can claim to be engineering professions as they meet this description of Engineering that I just quoted. Software and Computer Engineers apply scientific (mostly mathematical, or even Computer Science if you want) and technical knowledge to solve problems. They use experience and so no to apply this to the task at hand. They also do a lot of design work and the actual production of the software/hardware.
Computer programming vs. Software Engineering vs. Software Development
As a job title. Sure your official job title may be “Computer Programmer” or you may graduate with a “Computer Science” degree. That doesn’t mean you never do any “engineering”.
====
My opinion of what is generally understood by “Engineering” as a profession is (to quote Wikipedia here), “Engineering is the application of scientific and technical knowledge to solve human problems. Engineers use imagination, judgement, reasoning and experience to apply science, technology, mathematics, and practical experience. The result is the design, production, and operation of useful objects or processes.” And of course as a profession it comes with all the things that make it a professions such as responsibility to the public, client’s interest, public trust, an so on.
======
2/3. ACM Code of Ethics/Therac 25
- The ACM Code of Ethics and Professional Conduct has the general ethical principles which ACM members must abide to. It also has the code of conduct part called ‘more specific professional responsibilities’ tell you what you should do in particular (but still general) situations.
- Section 1 Ethical Principles
- Contribute to society and human well-being.
- Avoid harm to others
- Be honest and trustworthy (was Cindy honest to her superiors about the tests?)
- Be fair and take action not to discriminate
- respect privacy
- honour confidentiality
- Section 2 Specific Prof Responsibilities
- professional competence
- Give comprehensive and thorough evaluations of computer systems and their impacts, including analysis of possible risks.
- “computing professionals must minimise malfunctions by following generally accepted standards for system design and testing.”
- Access computing and communication resources only when authorised to do so.
- Section 1 Ethical Principles
- Killer Robot
- Randy Samuels
- Cindy
- The Therac 25 accidence were exactly that, they were accidents.
- The people involved were involved appear to have acted as per the ACM Code of Ethics and Professional Conduct.
- Sure they could have done things better. Improved processes, done more checks, get it independently tested, acted on patient complaints.
- Really?
4. Technical Issues with the Therac 25 Case
- Therac 25 was a machine for treating cancer
- Had no mechanical locks like previous models
- Reused software designed for older models
- relied more on software than hardware (did they take this into account when designing the software?)
- investigations only began after several accidents
- causes
- software not independently tested
- user manual did not explain certain errors
At the end of the day (as with many famous disasters) there were many times where if something was done better the problem may not have occured.
6. Killer Robot
- Cindy Yardley – Faked software tests to save her co-workers jobs.
- Knowingly let the product ship with flaws.
- Thought it would be okay, but be open and let the people charge decide that.
- —
- “Give comprehensive and thorough evaluations of computer systems and their impacts, including analysis of possible risks.”
Randy Samuels – Wrote the code that cause the robot to malfunction.
8. Intellectual Property
- Do people still use Windows 3.1? Can you still buy it? Its economic value now is probably close to zero. Why is it still protected then?
If copyright was designed to encourage new works then surly by freeing up old works such as Windows 3.1 gives Microsoft an incentive to make something new and better. - Creativity always builds on the past, yet we cannot make derivative works because of copyright laws.
- Data is now protected. And any situations that are not clear may take $$$’s to be decided by the courts. Need better statutory law and modern.
- Scientific knowledge. Most is public knowledge allows ideas to be examined and challenged and improved. Increasingly this is becoming private with genetic engineering.
- What if the internet was patented. Consider a) they essentially stoped all developments or b) make $$$’s from it when obviously we needn’t’ that cost for it to work. Inner workings were shared without the need for patents.
- Think much open source software.
From an ethical analysis,
- some 3rd world people have to pay to use seeds that have been freely available to them for centuries (this is very anti-utilitarian).
Affects Computer Scientists and Software Engineers.
- GIF Patent
- eg. iPhone developer not allowed to use CityRail data
- When copyright laws are used in this way to stop the spread of information then it counters many ethical principles, openness, fairness, sharing of information, helping someone when doing so will do no harm to you
From an economic view,
- Making a copy does no harm (negative benefit) to the person you copy from. Compared to stealing which takes it away from them. At most you may be removing potential sales.
9. Datavallience
Two types of dataveillance.
- Personal Surveillance (singled out)
- Mass Surveillance
Three examples,
- Government monitoring of internet traffic. (spying)
- Data collection of online services. (eg. facebook data gathering)
- Employer monitoring employee email.
Professionals have a responsibility to act in the public’s interest (as well as the clients interest). They also have codes of ethics to adhear to. Many ethical principles would lead to the conclusion that the people who are having their information monitored should be notified of this. To act in the public interest, the public needs to know when they are being monitored. This gives them the choice, to either use encryption, stop using the service, or something else. However professionals should make an exception to this rule when the matter is of national security or something other when it can be justified that not notifying is acting in the publics interest. This is what ethics is all about. Dealing with these exceptions to the rule.
- What is dataveillance?
- Is it immoral to collect data about other people?
- What personal data is currently being collected?
- What new opportunities are there to collect even more personal data?
- How can dataveillance be regulated?
- What advice would you give to non-specialists about safeguarding personal information?
It depends on the situation. The ethical approach I subscribe to is that the person who is having data collected on them, should be made aware of what is being collected, and that it is being collected.
Question 3: Lecture Questions
- give an overview of the lecture;
- describe the important professional and/or ethical ideas raised in the lecture, especially those that impact on Software/Computer Engineers and Computer Scientists;
- Important answer any specific questions attached below to the lecture.
1. Theoretical Underpinnings of Ethics
“Essentially, you are being asked to demonstrate how different ethical principles could be used to produce different outcomes. The important part of your answer will be the identification of the different principles and how your reasoning would proceed from those principles.”
Overview
- Humans around the world all tend to have the same ethical concepts. Integrity, fairness, honesty, openness…
- Relativism is doing what the culture is doing just because everyone else is doing it. This does not make it right. People are too quick to play this relative card.
- When we talk about ethics we mean prescriptive ethics. This is what you should or ought to do, compared to descriptive ethic which is what people do do.
- Ethical can be contrasted to,
- prudential (self interest)
- political (vote of opinion)
- preference (want rather than should)
- Rule, Consequences, Professional Code, law, loyalty to employer, confidentiality all factor into ethics. Rules and consequences fall into private (individual) morality, the rest is public morality which matters when you occupy a role.
- There are different levels of morality. In order,
- Obligation (signed agreement)
- Duty (eg. its your duty to treat every human with respect)
- Social Responsibility (duty without specific target)
- Minimally Decent Samaritan (go the extra mile to help them)
- Good Samaritan (someone asks you the time, you tell them)
- Heroism/Self-Sacrifice (wistleblowing)
And now on to the part relevant the the question at hand,
- Two different ethical principles are consequential (teleological) and non-consequential (deontological).
- Under the non-consequential view,
- to determine if an act is right or wrong it in fact has nothing to do with the consequences of the act. Instead it has to do with other things such as rights, duties, contracts, fairness, etc.
- Kant’s idea was that good will is what makes an act right, where good will is recognising your duty and then being able to make yourself do it (eg. you crash into a parked car you realise it is your duty to leave your details and then your able to make yourself to do that, even if you don’t want to do it).
- Under the consequential view,
- Acts are right based on their consequences.
- We have,
- Utilitarianism – “Acts are right insofar they produce happiness and they are wrong insofar as they don’t produce happiness.”
- Nationalism – “Acts are right if they are in the best interest of the nation as a whole.”
- Epistemism – “Acts are right insofar as they advance our knowledge, and they are wrong if they don’t do that.”
- Example. A dangerous criminal who commited murder and who is very likely to do it again falls into a dangerous situation (eg. is downing). It may very well be your social obligation to throw them an inflatable tube. That would be the fair thing to do, and it would be your social responsibility. However that would not be considering the consequences. Taking a consequential approach, the consequences of saving this one person may cause great unhappiness (and great risk of harm) for the people who the drowning person has threatened to kill. The ethical thing here may be to let him drown in order to save the lives of many others. But again this all depends on your ethical principles.
To make a moral judgement you need to make a judgement, have some justification for that judgement, and also have some principle that lead you to believe that that justification was right. (judgement > justification > principle) If you don’t have this, you don’t have a moral judgement.
2. Professionalism and Ethical Responsibilities
- The key thing that distinguishes professionals or a ‘profession’ is professionals have these extra public ethical responsibilities.
- act in client’s interest
- exercise of judgement
- code of ethics
- public trust
- act in public interest
- This is what separates a profession from a business (or a professional from a businessman). These extra things are their duty. Professionals have an obligation to oblige to these things. cf. businessmen are not ethically obliged to act in the public’s interest.
- They have a duty to survey the whole landscape and do what is best.
- Conflict of interest. You can’t be a profession if you have some extra incentive (eg. being paid to do something against the client and public’s interest).
“A person’s having a conflict of interest is not the same thing as a person’s being affected by a conflict of interest.” People who say they don’t have a conflict of interest just because they are not affected by (or more specifically their judgement is not affected by) a conflict of interest doesn’t
mean they don’t have a conflict of interest. - Codes of Ethics and Codes of Conduct. Codes of Ethics have values/principles. (eg. honesty, openness)
- Any principle/value will require judgement.
- You make a judgement on the principle/value, and in this respect Code’s of Ethics are empowering. (eg. guy here to kill someone, honesty does not require you to tell him where to find the person).
- Code’s of Conduct are different. They are not for introducing new values. They are there to remove judgement. They tell you exactly what to do in specific situations. eg. Bribes. They may say that you cannot accept any gift you receive over a given about. They take the heat off.
Other things of interest,
- “At work, you don’t leave your private, personal values at the door!” “Your ethical values must be there.”
- The answer to “Who’s to judge” is always “You, as an individual.” (from whatever perspective whether it be legal, ethical…)
3. Open source from an Economical Approach
- Software is a Collective Consumption Good. Consumption by one consumer does not reduce consumption by any other. Also “non rivalrous”.
- Software is Nonexcludable = difficult to exclude others from use
- Goods which are both lead to incentive to free ride, Results in “Market Failure”
- Argument is that, therefore software will not be produced unless there are special rights restricting the exploitation of software.
- According to this, these are not possible
- Linux, Apache, MySQL, PHP, Email, Internet protocols
Closed source (Sales Force): For every $1 spent on software development, $10 is spent on marketing
Open Source (SugarCRM): for every $4 spent on development, $1 is spent on marketing
6. Freehills Talk/Software Patents
Quick Summary
- Patents are a business tool.
- Monopoly vs. Secrecy
- Patentability (any prior art)
Ethical issues for Software Engineers/Computer Scientists
- Patents cost $$$, and take time. Is this worth it.
- What if the internet was patented. Consider a) they essentially stoped all developments or b) make $$$’s from it when obviously we needn’t’ that cost for it to work. Inner workings were shared without the need for patents.
- Think much open source software.
This comes down to your ethical principles. My ethical principle resolve around helping others, advancing knowledge, and working together for maximum benefit. So under my ethics software patents are unethical because they hinder the progress and development of (in the case of software patents), software. For example, someone patents the GIF encoding scheme, this can be used to lock out people from using this method. It also locks the scheme up so in the theoretical case where someone patents X, which lasts for 20 years. Person B invents X two years later but cannot use or distribute that invention because of the patent.
If you don’t want others exploiting or using or building on your invention then don’t share the details with anyone.
We are forgetting that many people (think Linux) don’t need the incentive of a patent to invent things or make them useful to the public. Patents hinder the publics access to certain processes.
If everyone was free to take others hard work and put it to good use, and build upon it and share that then progress would move faster than ever before.
But this is just my view of the matter. I do grant that I have this view because for me, progress (in terms of new and better software, etc) comes by people working on their own will because they want to for the fun of it (an example open source software, much of it was done with little commercial incentive). No money is wasted on lawyers who make no progress to the field. Instead everyone can work on pushing progress forward.
The ethics is solid. In fact patents were originally designed very ethically. Look at the consequential utilitarianism approach.
But things have changed. Software patents have not helped with this.
- Look at Mathematics > no patents. Much progress. Much work is based on previous work. (imagine if some theorems were ‘protected’ for 20 years and you could not discover any theorems that used that original theorem in its conception or proof)
- Have Software Patents really done what the patent was meant to do? No. The consequences of having patents was originally that the inner workings and methods of creation of an invention were published to the public for their good. But patents don’t have source code
Back to patents.
7. Law
- Statutory Law. Parliament.
- Common Law Courts.
- 4 jurisdictions
- criminal
- civil (tort and contract)
- administrative law
- equity
- litigation is the process or a lawsuit
- burden is on the plaintiff (the one brining the action)
- can be $$$
- putative damages (in contrast to compensatory damages) are not to compensate rather to reform or deter the defendant/others from doing the act/repeating it.
- Windows and the iPhone are licensed. They come with a license agreement.
Well as an ethical professional engineer you have an obligation/duty to act in the client’s and the public’s interest. As such you should notify the company of the situation and let them make a decision based on that. This is acting in the clients interest. Even with out this certain ethical principles such as openness may require you to notify the other party
Contrasted to an ordinary businessman who has no duty (thought they ought to do at least what is minimally decent) to act in the publics interest.
Different Standards when choosing to obey a law or not. Illegal? Litigation Risk? ‘Professional’ Standard(will your peers reject you)? Ethics(will your friends and children reject you)?
9. Internet Censorship
Overview
Professional/Ethical Ideas / Social/Technical
- There is a lot to talk about this topic.
- Censorship.
- Should there be any censorship?
- Internet Content Classification.
- Should there be a gov department which pro-actively classifies all the sites on the web? eg. DET. From a technical view, the web is huge and dynamic. There is no way that one gov department can keep up with this. eg. 20 hours of video is uploaded to youtube every minute.
- Should classification work on a complaint system? People who oppose could just flood it.
- Two other options.
- Community classification (rely on good faith, ie allow people to label certain URL’s as adult only… if you get enough people to ‘vote’ then the results should be good).
- Host classification. Make laws that require the content host to label any content they make available online.
- From an ethical standpoint, your ethical values/principles (mine do) may require you to at least make a reasonable attempt to provide users with classification information.
- Transparency is one of the criticisms. If decisions are made behind a closed door then this leads to abuse (eg. blocking political speech). Need public scrutiny and pressure to keep it in line. Taking a non-consequential ethical approach we need transparency for this scheme to meet the ethical principles of openness, fairness, honesty, integrity and so on. From a consequential approach, much research would need to be undertaken to consider the consequences, and this is something the governments reports should address. With the research in hand and from a utilitarian approach would censorship with no transparency produce the most happiness, or from an epistemic approach would this case of censorship without transparency really advance knowledge more than no censorship or censorship with transparency?
- This is real and at the end of the day it is computer scientists or software engineers that will implement any censorship. As such in the end it will come to these people to make an ethical decision on whether what they are doing is ethically right under their principles.
A social issue is over-legislating. eg. . For example certain materials (which probably includes child pornography) is illegal to view, so if you happen to accidentally find this material on the internet and you want to report it to the police so they can track down the perpetrator, you are in a conundrum. If you tell the police about it, then you must have viewed the material yourself which is illegal so you may face criminal charges, hence you cannot report it.
Another social issue. Is it just illegal content? Should the government be deciding what to view or not?
Technical Issue. What about things like VPN’s, tor…? The internet is huge and dynamic? What about a tag system.
The Cause of Slow Loading WordPress Pages Over https
For as long as I could remember, loading pages in my wordpress.com blog dashboard was really slow. I should have realised what was happening sooner but I never took the time to investigate. Whether I went to the edit posts page (/wp-admin/edit.php), new post (/wp-admin/post-new.php) there seemed to be numerous connections back to wordpress.com once parts of the page were loaded. These requests were to s-ssl.wordpress.com. Taking a look at the source, all the css and js files linked to from the html of the page were over the https protocol, and rightly so because I always go over the https protocol. What I didn’t realise is that Firefox will not cache files from https by default. So if I go to about:config and change browser.cache.disk_cache_ssl to true then these static css and js files will be cached. I restart my browers and all of a sudden pages load much faster and much more tolerable. The only problem is that its not just css and js files transfered over https that are cached but html files as well. I’m not sure how to get Firefox just to cache css and js files from https, but I have to leave that for another day.
COMP2121 Quick Summary on Particular Aspects
Von-Newman vs. Harvard Architecture.
Von-Newman has a single memory space, share for data and program instructions. Harvard Architecture has separate memory spaces for data and instructions (so you cannot execute from the data memory).
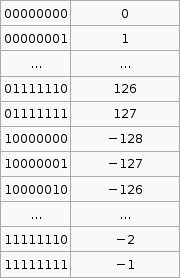
2’s compliment
It is important to know that the hardware does all arithmetic in 2’s compliment. It is up to the programmer to interpret the number as signed or unsigned.
To convert a number from 2’s compliment, for example -45 in 2’s compliment is 11010011, we can do something like this,
To go the other way from say -1 to the 2’s compliment form 11111111 we use that formula. I’m not exactly sure how its supposed to work so I’ve hacked it to make it work.
If the number you wish to convert is negative, let , so that X is positive then take
where p is the number of bits you are using (say 8), then subtract X. If the number to convert is less than
(where p is the number of bits, say 8 ) then leave it as is and that in your 2’s compliment.
Now that was complicated. But its the only way I can get that advertised formula to work with the given set of sample data (as in that table above).
Sign Extension
Why do we need sign extension? We need it in order to do operations on numbers than have different bit lengths (the number of bits used to represent the number).
Decimal to Binary
From a human kind of approach to convert 221 to binary, we see that , that is 7 is the largest power of 2 less than 221, so we have
. That gives us 128, so we still have 93 (221-128) to go. We try
, this is less than 93. So far we have
. 29 left now, but
is greater than 29, so we put a zero in that digit, ie.
. If we go on we get
. Taking the coefficients of the
terms we get the number 221 in binary, 11011101.
We can convert hexadecimal to binary by going from hex to decimal then decimal to binary. For hex to decimal,
(where F23AC is in hex and 992172 is in decimal)
Operations on Signed and Unsigned Multi byte Numbers
add al, bl adc ah, bh does a + b, result in is a.
There are 3 multiplication operations, MUL (Multiply Unsigned), MULS (Multiply Signed) and MULSU (Multiply Signed with Unsigned). They each do this. Notice the result is stored in r1:r0.
Thus to do n*m = r where n is 2 bytes unsigned and m is 1 byte signed, mulsu nl, m ;nl * (signed)m movw rh:rl, r1:r0 mulsu nh, m ;(signed)nh * m add rh, r0
We can also do 16bit * 16bit,
;* From AVR Instruction Set Guide, pg 99-100. ;* Signed multiply of two 16-bit numbers with 32-bit result. ;* r19:r18:r17:r16 = r23:r22 * r21:r20 muls16x16_32: clr r2 muls r23, r21 ;(signed)ah * (signed)bh movw r19:r18, r1:r0 mul r22, r20 ;al * bl movw r17:r16, r1:r0 mulsu r23, r20 ;(signed)ah * bl sbc r19, r2 add r17, r0 adc r18, r1 adc r19, r2 mulsu r21, r22 ;(signed)bh * al sbc r19, r2 add r17, r0 adc r18, r1 adc r19, r2 ret
brge and brsh
- brge is Branch if Greater or Equal, Signed.
if () then branch.
When you do cp Rd, Rr then brge, the branch will be taken if RdRr, where Rd and Rr are taken to be signed numbers.
- brsh is Branch if Same or Higher.
if () then branch.
When you do cp Rd, Rr then brsh, the branch will be taken if RdRr, where Rd and Rr are taken to be unsigned numbers.
Calculating Total Stack Space Needed
Draw a call tree, find the path with the most total weight, that total weight is the total stack size needed. Here is the sample question,
A C program consists of five functions. Their calling relations are shown as follows (the arguments and irrelevant C statements are omitted).
int main(void) {…func1(…);func2(…);…}int func1(…) { … func1(…); … } int func2(…) { … func3(…); func4(…); … }func1() is a recursive function and calls itself 15 times for the actual parameters given in main(). Both func3() and func4() do not call any function. The sizes of all stack frames are shown as follows.
main(): 200 bytes.
func1(): 100 bytes.
func2(): 400 bytes.
func3(): 1,400 bytes.
func4(): 300 bytes.How much stack space is needed to execute this program correctly? (3 marks)
| main() func1() func1() x 15 200+100+15×100 =1800 |
main() func2() func3() 200+400+1400 =2000 |
main() func2() func4() 200+400+300 =900 |
The path with the most total weight is main() > func2() > func3(), so this is the total stack space needed.
Nested Interrupts
 (Source: Hui Wu’s Lecture Notes)
(Source: Hui Wu’s Lecture Notes)
Keypads with ‘abc’ ‘def’ … buttons
These keypads where to enter b you need to press the abc button twice in succession, but wait to long at it will chose a. Here is a psudo algorithm that seemed to fit this,
.def reg = rN
.def reg = rM
.def count = rX
//passvalue means that we register the given value ie. abc abc wait > b
setup:
clr reg (to some value that is != to a key value) ;set to default
clr count
rjmp keyloop
keyloop:
check pins for a key
if no key pressed rjmp keyloop, else continue
//key was pressed, and value is stored in key
reset someTimeCounter
if (key == reg) {
inc count
if (count == 3)
passvalue(reg,count)
}else{
if (reg != default) ;so we don't initially passvalue
passvalue(reg,count) ;send the last value
reg = key ;store the new one
count = 1
}
rjmp keyloop
if someTimeCounter expires and count != 0 //(count up, so expires after time to wait for anymore keypresses) (check count != 0, because if its 0 then we never had any key pressed that we need to send)
passvalue(reg,count)
reg = default
Switch Bounce Software Solution
When a switch makes contact, its mechanical springiness will cause the contact to bounce, or make and break, for a few millisecond (typically 5 to 10 ms). Two software solutions are wait and see and counter-based.
- If we detect it as closed, wait for a little bit and check again.
- Poll the switch constantly. For each poll if the switch is closed increment the counter. If we reach a certain value in a certain time then the switch was closed (or button pressed).
Serial Communication (Start and Stop bit)
“[The] start bit is used to indicate the start of a frame. Without the start bit, the receiver cannot distinguish between the idle line and the 1 bit because both are logical one. A stop bit is used to allow the receiver to transfer the data from the receive buffer to the memory.” (Wu, Homework 6 Solutions)
UART
 (Source: Hui Wu, Lecture Notes)
(Source: Hui Wu, Lecture Notes)
Sample Q3a
(This code probably won’t work and probably has errors (and maybe not just simple ones, but serious ones that mean that the logic is wrong))
.dseg A: .byte 20 ;array of size 10, element size 2 bytes .cseg ldi XL, low(A) ldi XH, high(A) ;add the contents of the array. store 0 store 1 store 2 store 3 store 4 store 5 store 6 store 7 store 8 store 9 ;find the largest value ldi XL, low(A) ldi XH, high(A) ;start with the 1st element of the array ld r25, X+ ld r26, X+ ldi r20, 10 ;size of array loop: cpi r20, 0 breq endloop ld r21, X+ ld r22, X+ cp r25, r21 cpc r26, c22 brlo lowerthan ;we have a new max mov r25, r21 mov r26, r22 lowerthan: inc r20 rjmp loop endloop: rjmp endloop .macro store ldi r16, low(@0) ldi r17, high(@0) st X+, r16 st X+, r17 .endmacro
For some reason in my lecture notes I have “eg. fine 2nd or 3rd smallest or largest” so here is a modification to do something like that.
.dseg A: .byte 20 ;array of size 10, element size 2 bytes .cseg ldi XL, low(A) ldi XH, high(A) ;add the contents of the array. store 0 store 1 store 2 store 3 store 4 store 5 store 6 store 7 store 8 store 9 ;sort into accending loopthough for the length of array, (by then we can be sure its sorted) ldi r23, 10 largeloop: cpi r23, 0 breq endlargeloop ;point X to the start of A ldi XL, low(A) ldi XH, high(A) ;start with the 1st element of the array ld r25, X+ ld r26, X+ ldi r20, 10 ;size of array loop: cpi r20, 0 breq endloop ;the next value ld r21, X+ ld r22, X+ cp r25, r21 cpc r26, c22 brge gethan ;r22:r21 < r26:r25 ;swap the order st -X, r26 st -X, r25 st -X, r22 st -X, r21 ld r24, X+ ;to change the X pointer ld r24, X+ ld r25, X+ ld r26, X+ gethan: inc r20 rjmp loop endloop: endlargeloop: inf: rjmp inf .macro store ldi r16, low(@0) ldi r17, high(@0) st X+, r16 st X+, r17 .endmacro
COMP2121 – Wk05 – Interrupts
To explain interrupts, Wu used an example of a network card that is downloading a file. The network card has a buffer, and only once this buffer is full (or data stream is complete) should the CPU then copy the contents from the buffer to the RAM. So how does the CPU know when the network card’s buffer is full and when to execute the copy? He described two ways here interrupt and polling.
Polling involves the CPU periodically asking the network card, are you full? Two problems with this method are a) there may be a delay as you have to wait for the poll request to be made and b) it wastes a lot of CPU time. Polling is implemented in software, not hardware.
An alternative to polling is using interrupts whereby the network card will send an interrupt signal to the CPU to get its attention. This needs special hardware to implement, however it is very efficient compared with polling.
An interrupt system must (among other things),
- Wait for the current instruction to finish before taking care of the interrupt.
- Return to the interrupted program at the point where it was interrupted.
- Signal the interrupting device with an acknowledge signal when the interrupt has been recognised.
IRQ is an interrupt request signal.
A daisy chain arrangement (as seen below) allows multiple devices to send and IRQ. However the CPU cannot determine from the IRQ line which device sent the interrupt. So in a daisy chain system when the CPU receives an IRQ, it will send a signal to IO1 asking “did you send the IRQ?” if IO1 sent the request it will reply “yes”, if not it will pass the question on to the next IO device and so on. The response is passed back in the same way.
Reset is an interrupt in AVR, and in the AVR Mega64 there are five different sources of reset. There is a flag in the MCU Control Register for each of these and can be used to determine the source of a reset interrupt. The watchdog timer is one source of reset.
Watchdog Timer
The watchdog timer is used to try to reset the system if an error such hang occurs. The watchdog timer in AVR can be enabled or disabled.
If the Watchdog timer is enabled, it needs to be periodically reset using the wdr instruction. When (if) the Watchdog times out, it will generate a short reset pulse.
Channel TEN’s contractor/outsourcer/… Posts TV Show Online Before It Airs
It seems that channel ten (or at least their contractor/outsourcer/whatever) decided to release episodes of a show its airing (Merlin) on the interent before their have aired on TV. Its not such a big deal because the show has already aired in the UK, but I would still say good on you channel 10 for going that extra mile and supporting the fans who want to watch the show through legal methods.
The links are (its a 13 episode season),
???
???
???
But they are sure to change, esp the dates (but they were valid when I posted them (wget -S –spider filename, will verify if a file exists for you)), so you may need to change them (the dates) (ps. DownThemAll is great at trying many different file names to see which ones get a hit). On ten’s web site they only list the most recent episode but if you look at your HTTP logs you can see the flv URL. There is no key in the file so you should be able to just change the episode number and then try all dates in the near months.
PS. In the odd chance than someone from TEN reads this you should note that Australia has poor interent (in terms of IP quota) as such we have a greater need to be able to download shows and watch later (so the download can be done off peak, or from a location with more generous IP quota). You should consider promoting friendly file formats straight for download. Perhaps then you will have a larger uptake of online viewers (I would find a short advertisement at the start and/or end of the video acceptable).
PSS. I’m not one of those people who thinks posting links to pirated material should be (or is) illegal or immoral. Among many other reasons, how is the person who posts the link supposed to know if the material they are linking to is infringing?
PSSS. This is not a vunrability and as such I don’t think I am required under my own ethics to let them know. But regardless this is obviously intentional, and dispite all this I cannot report it to TEN anyway as there is no email listed on their contact us page.




Re: 7.30 Report “Uncertain future for newspapers”
Going through the backlog. Just a few comments on the 7.30 Report story (transcript) (video sorry for the format but its all I could see, I don’t know where I got my m4v one from).
Very interesting stuff here, but I have a couple of points. Mind you I don’t have much experience here, I’m not a journalist or an economist…
1. Government Subsidiary for Quality Journalism
One of my main concerns here is that you have two negative forces. On one hand you have the government paying for investigative journalism, but those journalists are having to fight the government to get the story to break. Would there be a need for investigative journalism in the government arena if the government was more open? You wouldn’t need the journalist filing freedom of information requests if the department put this info into the public domain by default. The solution is for the government to be more open and transparent, something which they seem to do a lot of talk about (and are doing some things that make them open), but not nearly enough.
But the government or the government departments are probably unwilling to put information out there that may embarras them. Unfortuantly you probably need so driving for that motivates government departments to be more open. I see an online “village pump” where the community can gather and build up in numbers to support certain movements (such as access to certain statistics that may be part of a journalists investigation). Those numbers are a force that could provide pressure for an unwilling government department.
2. Coverage
Nick Davies said that “what you haven’t got is citizen journalists covering the courts or the government departments or the police or the hospitals or the schools or doing investigations.” He quoted lack of “skills, time or resources” as the reason for this. I don’t believe this. A large chuck of the feeds I subscribe to are citizens blogging about copyright decisions made in court. Perhaps it is lack of cooperation of the government department. For example they charge huge unreasonable fees for your FOI application. I don’t see the solution as get a big company who can pay the fees, rather use some other methods to pressure the department into providing the information needed for investigative journalism free or charge, free for all.